Are email attachments secure? The short answer is: not always.
They can be risky due to malware, phishing, and data breaches. Email attachments are a common part of our digital lives. We use them to share documents, images, and other files. But these attachments can pose security risks. Hackers often use them to spread malware or steal sensitive information.
Understanding these risks is crucial. It helps you protect your data and stay safe online. In this blog, we’ll explore the security of email attachments. We will discuss common threats and offer tips to safeguard your information. Stay with us to learn more about keeping your email attachments secure.
Email Attachments Security Risks
Email attachments are a common way to share documents, images, and other files. However, they come with their own set of security risks. Understanding these risks can help you protect your personal and professional information.
Common Threats
Opening an email attachment from an unknown sender can be dangerous. Cybercriminals often use email attachments to spread malware and viruses. These can steal your data, lock your files, or even take control of your computer.
Phishing attacks are another common threat. These emails look like they come from a trusted source. But they trick you into giving away sensitive information.
Even attachments from known contacts can be risky. Their accounts might have been hacked. Always verify before opening any attachment.
Types Of Malicious Attachments
Not all email attachments are the same. Some are more dangerous than others. Here are a few types to watch out for:
- Executable files (.exe): These can install harmful software on your computer. Avoid opening them unless you are sure they are safe.
- Documents with macros (.docm, .xlsm): These can run malicious code. Disable macros in your settings to stay safe.
- Compressed files (.zip, .rar): These can hide malicious files. Scan them with antivirus software before opening.
Have you ever received a suspicious email attachment? Think twice before clicking. Your vigilance can keep your information secure.
Recognizing Suspicious Attachments
Emails with attachments can be risky. Recognizing suspicious attachments is vital to avoid malware and phishing scams. Spotting red flags helps protect your personal and professional data. Learn to identify these signs and examples to ensure your email security.
Red Flags To Watch For
Watch for unusual file extensions. Common ones like .exe, .bat, or .vbs may indicate malicious intent. Attachments with names that make no sense or are misspelled should raise concern.
Be cautious of unexpected emails from unknown senders. Legitimate companies rarely send attachments in unsolicited emails. Verify the sender’s email address and look for slight variations in spelling.
Attachments requesting sensitive information like passwords or bank details are suspicious. No reputable organization asks for such data through email attachments. Examine the message for urgency or fear tactics as these are common in phishing attempts.
Examples Of Phishing Emails
Phishing emails often mimic well-known companies. They may contain logos and branding but slight spelling or grammar mistakes are telltale signs. A common example is an email appearing from your bank asking to verify your account. It may include an attachment claiming to be a form.
Another example is an email posing as a package delivery notification. It claims a problem with your shipment and asks you to open an attached document to resolve the issue. These tactics aim to trick you into opening the attachment and releasing malware.
Emails that impersonate government agencies are also common. They might ask for personal information or threaten legal action. The attachment may claim to be an official document. Always verify the sender’s authenticity before opening such attachments.
Safe Practices For Sending Attachments
Sending email attachments can be risky. Files can be intercepted or accessed by unauthorized people. Using safe practices helps protect your data.
Two effective methods are encryption and password protection. These practices add layers of security to your files.
Encryption Techniques
Encryption converts your file into a secret code. Only those with the key can read it. Use tools like PGP or S/MIME for email encryption. These tools make your attachments unreadable to others.
Encrypting attachments before sending them ensures privacy. It’s a strong defense against hackers. Even if someone intercepts your email, they can’t access the encrypted files.
Password-protected Files
Password protection adds an extra layer of security. Before sending an attachment, create a password for the file. Share the password through a different channel, like a phone call or text message.
Many programs offer password protection. Use software like Microsoft Office or Adobe Acrobat. These allow you to set strong passwords for your files.
Using both encryption and password protection makes your attachments very secure. Together, they help keep your data safe from prying eyes.
Best Practices For Receiving Attachments
Email attachments can pose security risks. Always scan files with antivirus software before opening. Never download attachments from unknown senders.
Receiving email attachments can be a bit of a gamble. While they often contain important files, they can also pose significant security risks. To help you navigate these waters safely, here are some best practices for receiving attachments.Verifying Sender Identity
When you receive an email with an attachment, always verify the sender’s identity. Check the email address carefully. Look for any misspellings or irregularities. If the email comes from someone you know, but the content seems out of character, reach out to them through another communication method to confirm they sent the attachment.Remember, phishing attacks are common. Cybercriminals often impersonate legitimate contacts to trick you. Always be cautious.Using Antivirus Software
Antivirus software is your best friend when dealing with email attachments. Ensure your software is up-to-date. Scan every attachment before opening it.Most antivirus programs can automatically scan attachments. However, it’s good practice to manually scan files from unknown or unexpected sources. This extra step can prevent malware infections.Keep in mind, no single solution is foolproof. Combining vigilant practices with robust software enhances your security.By implementing these practices, you can protect yourself from the potential dangers lurking in email attachments. Always stay cautious and proactive. Your digital safety depends on it.Secure File Sharing Alternatives
Are you tired of worrying about the security of your email attachments? You’re not alone. Many people are looking for safer ways to share files. Let’s dive into some secure file sharing alternatives that can ease your concerns and improve your workflow.
Cloud Storage Solutions
Cloud storage solutions are a popular alternative to email attachments. Services like Google Drive, Dropbox, and OneDrive allow you to store files securely in the cloud. You can share links to these files with others instead of sending attachments.
These platforms offer robust security features. For example, you can set permissions to control who can view, edit, or download your files. Some services even provide end-to-end encryption for added security.
Have you ever shared a large file and worried about it getting lost in someone’s inbox? Cloud storage eliminates this issue. Your recipients can access the files directly from their browser, reducing the risk of email-related problems.
Collaborative Platforms
Collaborative platforms like Slack and Microsoft Teams provide secure file sharing options. These tools are designed to facilitate teamwork and often have built-in security measures.
Sharing files through these platforms ensures that your data is protected within a closed environment. You can share documents, spreadsheets, and presentations without worrying about them being intercepted by unauthorized parties.
These platforms also integrate with other tools you might already be using. This means you can share files directly from your cloud storage or other apps, streamlining your workflow.
Have you ever considered the benefits of using these alternatives? They not only enhance security but also improve efficiency and collaboration. What secure file sharing method will you try next?
Credit: www.spiceworks.com
Implementing Email Security Policies
Email attachments can pose significant security risks if not properly managed. Implementing strict email security policies helps protect against malware and phishing attacks. Secure your organization by carefully monitoring and controlling email attachments.
Implementing effective email security policies is crucial for any organization. By setting clear guidelines and providing proper training, you can protect sensitive data and prevent breaches. Let’s discuss how to create these policies and ensure everyone in your organization follows them.Company-wide Guidelines
Establishing company-wide email security guidelines is your first step. These guidelines should outline best practices for sending, receiving, and managing email attachments. Specify what types of files are safe and which should be avoided.Use simple rules. For instance, instruct employees to avoid opening attachments from unknown senders. Encourage the use of encrypted attachments for sensitive information. Make sure everyone knows how to report suspicious emails.Regularly update these guidelines. Cyber threats evolve, so your policies should too. Share updates through company-wide emails or intranet posts to keep everyone informed.Employee Training Programs
Training your employees is just as important as setting guidelines. Conduct regular training sessions to educate them about email security. Use real-life examples to show the consequences of ignoring these rules.Interactive workshops can be more effective than just handing out a manual. Encourage questions and discussions during these sessions. This helps employees understand the importance of security measures.Consider using simulations. Phishing tests can help employees recognize and respond to potential threats. Reward those who follow the guidelines and take the right actions.Remember, email security is a shared responsibility. By setting clear guidelines and providing continuous training, you can build a strong defense against cyber threats. How does your organization handle email security?Tools For Enhanced Email Security
Email attachments can pose security risks. Tools for enhanced email security help protect sensitive data from threats. These tools scan attachments for malware and encrypt content for safe transmission.
### Tools for Enhanced Email SecurityAre you concerned about the security of your email attachments? You’re not alone. Many individuals and businesses worry about sensitive information falling into the wrong hands. Fortunately, there are several tools to boost your email security.Below, we’ll dive into two essential categories: email encryption tools and secure email gateways.Email Encryption Tools
Encryption tools are essential for protecting your email attachments. They work by converting your data into a code that only authorized parties can decode. Additionally, understanding how to encrypt email attachments is crucial in safeguarding sensitive information from unauthorized access. Many email services offer built-in encryption features, while standalone software options provide added layers of security. By employing these tools, you ensure that your communications remain private and secure.Think of it as locking your message in a digital safe. Tools like ProtonMail and Tutanota offer end-to-end encryption, ensuring your attachments stay private.Even if someone intercepts your email, they can’t read the contents. This way, your sensitive information remains secure.Have you ever sent an email and worried about who might access it? With encryption tools, you can have peace of mind. These tools are user-friendly and require minimal setup, making them accessible for everyone.Secure Email Gateways
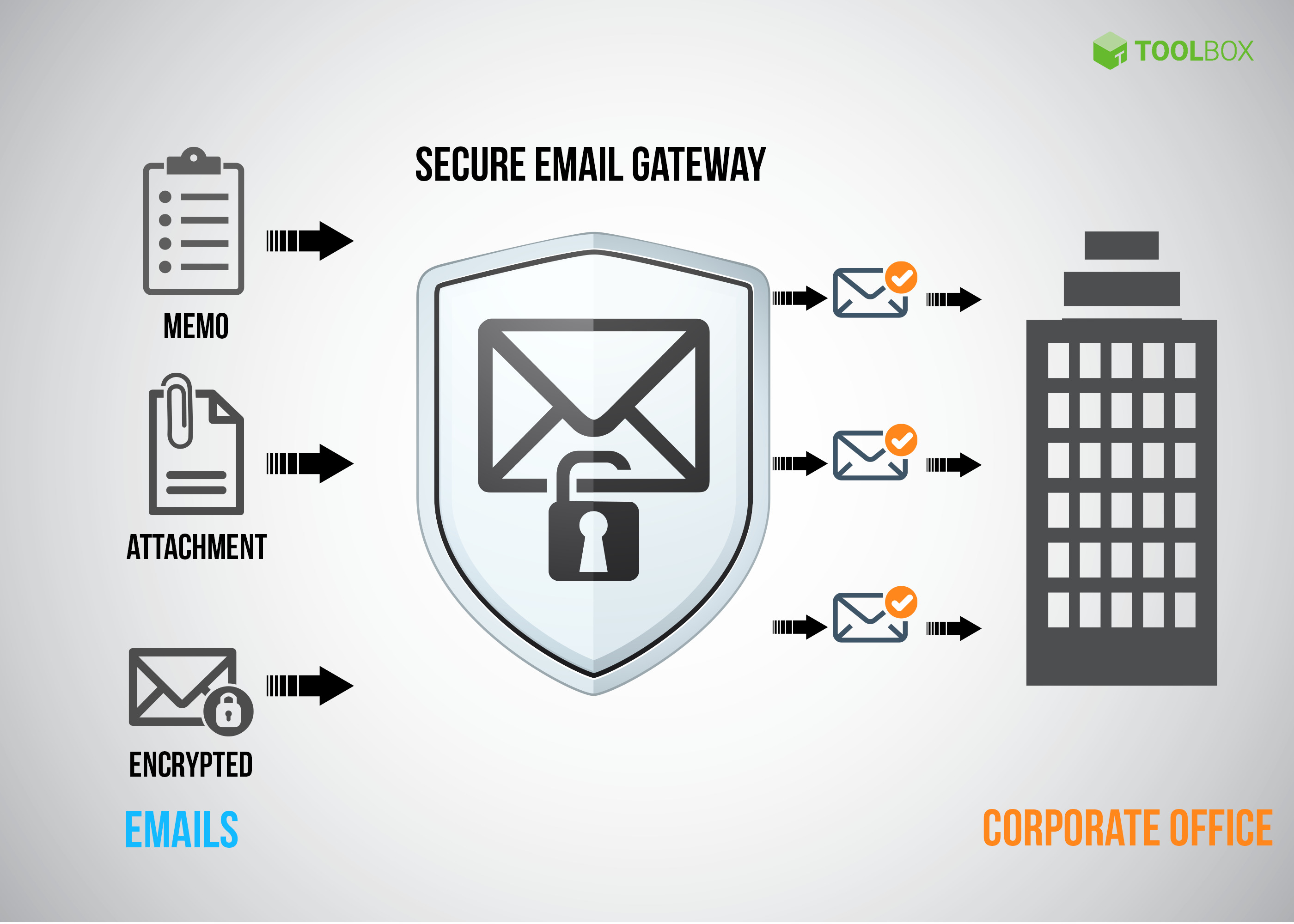
Another powerful tool for enhanced email security is the secure email gateway. These gateways act like security guards for your emails.They scan incoming and outgoing emails for threats, such as viruses and phishing attempts. Services like Mimecast and Proofpoint are popular choices.Imagine having a vigilant guard that examines every email for malicious content. This reduces the risk of malware and other cyber threats infiltrating your system.Are you tired of sifting through spam and worrying about potential threats? Secure email gateways offer a layer of protection, ensuring a safer email experience.These tools are especially valuable for businesses that handle large volumes of email. They provide an extra shield, keeping your communications secure.In conclusion, using email encryption tools and secure email gateways significantly enhances your email security. They provide the peace of mind you need when sharing sensitive information.So, are you ready to take your email security to the next level? Start using these tools today and protect your attachments from prying eyes.
Credit: community.pepperdine.edu
Responding To Security Breaches
Email attachments can be a significant security risk. Malicious attachments may compromise your system. Responding quickly and effectively to security breaches is crucial.
Immediate Actions
First, identify the breach source. Check recent emails and attachments. Disconnect affected devices from the internet. This prevents further data loss.
Next, change your passwords. Use strong and unique passwords. Inform your IT team about the breach. They can provide further assistance. Report the breach to relevant authorities. This ensures proper action is taken.
Long-term Solutions
Implementing long-term solutions helps prevent future breaches. Regularly update your software. This includes antivirus programs and firewalls. Educate your team about email security. Awareness reduces the chances of falling for scams.
Use encryption for sensitive emails. This adds an extra layer of security. Regularly back up your data. In case of a breach, you won’t lose important information.
Consider using a secure email service. These services offer additional security features. Regularly review and update your security policies. Stay informed about new threats and how to counter them.
Credit: votiro.com
Frequently Asked Questions
Is Sending Attachments Via Email Secure?
Sending attachments via email can be secure, but it depends on encryption. Always use trusted services and avoid sharing sensitive data. Consider using file-sharing platforms that offer end-to-end encryption for added security. Additionally, familiarize yourself with how to send secure attachments, as this can significantly reduce the risk of data breaches. Remember to verify the recipient’s identity before transmitting any sensitive information.
How Do I Send An Email Attachment Safely?
Ensure your antivirus software is up-to-date. Use strong passwords and encrypt sensitive files. Verify recipient’s email address. Avoid sharing personal information. Double-check attachments before sending.
Are Email Attachments Safe?
Email attachments can be risky. Always scan them with antivirus software. Avoid opening attachments from unknown senders. Check file extensions carefully.
What Is A Secure Way To Send Documents By Email?
Use encrypted email services, password-protect documents, and share the password via a separate method like a phone call.
Conclusion
Email attachments can be secure with the right precautions. Always use trusted sources. Encrypt sensitive files to add protection. Regularly update your antivirus software. Avoid opening attachments from unknown senders. Use strong passwords for added security. Stay informed about the latest security practices.
By taking these steps, you can keep your email attachments safer. Be vigilant and proactive in protecting your information.